Because different polls
may require different levels of security, PollMaker allows you to
determine the level of security that is right for your polls. If you
are collecting sensitive data, such as credit card information or
Social Security numbers, you would want to apply greater security
than you would if you were collecting anonymous data about the
personal interests of your respondents. PollMaker provides the
flexibility to address the security needs of your polling data and
your poll definitions.
PollMaker provides two
different features that together determine the level of security for
a poll:
EncryptKey Property
The EncryptKey property
is the first security feature provided by PollMaker. Using the
Properties Grid in Poll Designer (figure 1), you can set the value
of this property for a poll to either "True" or "False." When the
default setting of "False" is used, the poll result data files
generated by your poll are encrypted with a 48-bit strong encryption
algorithm using an application-defined cipher key (for more
information on poll result data files, see Manage Poll
Data). If you set the EncryptKey property to "True," the same
48-bit strong encryption algorithm is used to encrypt the poll
result data files, but you must provide a Master password (see Poll
Passwords below) that PollMaker uses as the cipher-key. These
encryption algorithms prevent your poll data from being accessed by
unauthorized persons.
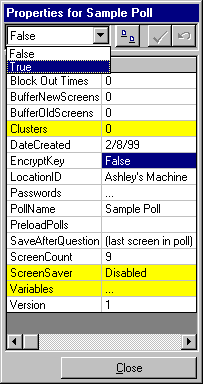
Figure 1: Poll Designer Properties Grid for a
Poll showing the EncryptKey Property
Poll
Passwords
PollMaker provides a
second security feature by allowing you to specify up to five
different passwords for a poll. Each of these passwords corresponds
to a different level of poll functionality. As a result, when one or
more of these passwords are specified, the actions that a person can
take in relation to the poll will be determined by the password that
he provides. The five passwords and their corresponding actions
include:
| Password |
Related Functionality |
Suggested Use |
| MASTER |
User may perform all actions within the poll |
Top-Level Personnel |
| EDIT |
User may edit the poll definition file which contains the
poll's structure |
Poll Designers and above |
| MANAGE |
User may manage poll's response data using Poll Manager,
including backing-up, restoring, exporting and dumping poll
results |
Mid-Level Personnel |
| RUN |
User may launch a poll on a kiosk |
Kiosk Operators and End-Level Personnel |
| REPORTS |
User may run poll reports but does not have full access to
the poll results data |
Kiosk Operators and End-Level
Personnel |
Therefore, if you have
personnel with different roles related to a poll, you can use
passwords to limit each person's actions to only those required by
her role. For example, if you have a person that is solely
responsible for running a poll on a kiosk, you can set the "Run"
password for that poll. When this person uses the "Run" password, he
can launch the poll, but he cannot change the poll design or view
the poll response data. In Poll Designer, you can set these
passwords in the Poll Passwords Dialog Box (figure 2).
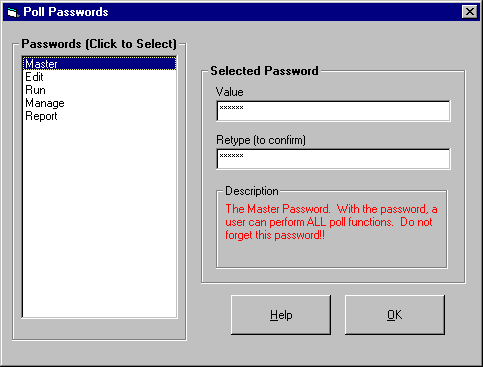
Figure 2: Poll Designer Poll Passwords Dialog
Box
Different Levels of
Security
The combination of
these two settings lets you determine the level of security that is
applied to a poll. The default settings of "False" for the
EncryptKey property and no poll passwords provide a minimum level of
security for all polls. This level of security provides protection
against the unauthorized viewing of your poll data files and is
adequate for the majority of polls. On the other end of the
spectrum, the maximum level of security for a poll is provided by
setting the EncryptKey property to "True." This setting requires
that you specify a Master password that will be used as the
cipher-key in the encryption algorithm. As a result, all poll
activities, from running the poll to editing the poll definition and
viewing the poll data, will require the Master password. This level
of encryption is stronger because a user provided cipher-key is used
versus an application specified cipher-key.
Intermediate levels of
security can be provided by setting the EncryptKey property to
"False" and utilizing one or more of the poll passwords. The base
level of encryption is applied to the poll data, but you can
restrict access to PollMaker functions depending on the passwords
that you use.
Even the minimum level
of security, provides strong protection for your poll data, but
PollMaker allows you to decide how much additional security is
required for your polls and polling data.
Return to Poll Management
and Execution.
|